Desktop Security Email Pro Help
Help Directory
Account Setup
Settings
Contacts
Encryption (E2EE)
Compose
Signatures, Snippets, Placeholders
Read
Read Email Authentications
Folders
Labels
Auto-Sort and Piority Inbox
Calendar/Tasks
Reply Request/Reminder
Adserver Trackers
Spy Pixel Tracking
Phish Scanner
Suspicious Attachments
Private Browser
Images (.heic, .avif)
Printing
Attributions
Account Setup
Both Outlook (Outlook, Live, Hotmail) and Gmail now use modern authentication (Oauth2) for all email client account verifications. This means no more passwords used. However, you must already have, on your machine, a Microsoft Account for Outlook emails or Google Gmail account for Gmail emails.
Account Create
In the left navigation bar, click the 4th icon to open the Accounts Page.
Follow these steps:
1. Select your PROVIDER
2. Enter your full EMAIL ADDRESS
3. Enter the DISPLAY NAME
4. Click button: + ADD
Your default browser window will open showing any accounts you have.
Select the proper email account and follow any more prompts.
You are then authorized when the provider sends the app your ‘Access Token’.
Please note, sometimes they will request a ‘Refreshing’ of your access token, so just follow the easy instructions.
Accounts Listing
Your accounts are listed on the left. The account at the top of the list is what loads at startup.
Use the up arrow button to change the order if desired.
Account Delete
Choose an account in the listing, click button: Delete
Settings
In the left navigation bar, click the bottom icon to open the Settings Page.
Logon and Email Read PIN
A PIN set-up here, is used for both initial app logon and to open and read each individual email.
After entering your PIN, you will need to also setup the 3 PIN recoveries. This requirement is because Quantanon does not store any PIN info in the cloud or any server. All is stored securely on your device. Therefore, it is imperative that you be able to unlock your app on your own.
The 3 recovery options:
1) Choose a security question, then enter your answer
2) Enter a recovery email. This must be an Outlook or Gmail account
3) Enter a 6 character minimum password
Once your PIN is set, toggle the switches to your desired setting.
The button: Reset PIN, is used to remove all PIN info.
Email Receive and Read
Check for new email in minutes
Set to ON and select MINUTES to automatically check for new emails
Play sound with new email arrival
Set to ON to hear a sound on new email arrivals
Adjust mail time
Enter a number other than zero if your email time stamps need adjusting for your part of the world
Display name for emails sent to self
Enter a short name for emails you send to yourself
Email Compose
Editor default font size
Enter a number for your default font size
Show ‘No Subject’ warning
Set to YES if you want a warning dialog to appear if no subject entered in compose email
Enable rt-click context menu in editor
If YES, may obstruct some format buttons, not a big deal, you decide
In Reply All – any Cc, are also replied as Cc, else as To
Set to YES if you want to reply as Cc
Select Attachment Image Size
Set desired compress size (320,640,1280), or original (big and slow)
The maximum attachment size for Gmail is 25 MB.
The maximum attachment size for Outlook is 20 MB.
Add Signature to all emails
Select YES and add signature text
Send Encrypted iniially checked
When you click the ‘New’ email button, this is already checked
Security Related
Email messages read mode
Set desired mode for reading. Safest is Text Only, but images will not show.
Clicked Link UTM Parameter + Cleaning
Set to ENABLE to clean all clicked and pasted links
On Clicked Links – Show Browser Options
If YES, all installed browsers will show in a choice list
Show attachment suspicious extension alert
If YES, a warning dialog will appear, giving you ‘pause’ to think and examine the email
Contacts
Contacts are managed in the window, Manage Contacts, 6th icon in the left navigation pane.
Tab: Individual Contacts
Section: Create Contact
1) Select email address from list or type in manually
2) Enter a display name for contact
3) Check box ‘Favorite’ to have this person show at top of contacts send list
4) Press ‘Add Contact’
5) Contact now shows in the left column listing
Section: Edit Contact
1) Right-click contact in the listing
2) Select ‘Edit Contact’ (Edit Contact sub tab opens)
3) Edit address, display name, and/or favorite status
4) Press ‘Edit Contact’
Section: Delete Contact
1) Right-click contact in the listing
2) Select ‘Delete’
3) Confirmation window appears
4) Select ‘Yes, delete’
A contact may also be added 2 more ways:
1) In the Compose Page, click button: + Add Contact, and type in the info
2) In the Manage Contacts Page, set the ‘Auto-Add contacts on email reply’ to Yes
Tab: Grouped Contacts
Conveniently, you can create groups of contacts, using a name of your choice, then in the Compose Window, you can use the button ‘Grouped Contacts’ to add your multiple contact group all at once to the recipient list.
Section: Create Group Name, Group, Edit
Add Group Name
1. Click sub-tab: Group Names
2. At the bottom, enter a new group name
3. Press button: + Add
4. Group name appears in the listing above
Delete Group Name
1). Click sub-tab: Group Names
2. In the listing, select the name
3. Press button: Delete (if contacts in group, delete them from the listing first)
Create Grouping
1. Click sub-tab : Create Grouping
2. Select desired contact from the drop-down list
3. Select email send type (To, Cc, Bcc)
4. Select group name from the drop-down list
5. Press button: + Add Grouping
Viewing Groupings
In the left column listing, you will see the groups clustered together in order. The group name is in bold.
Edit Grouping
1. In the Grouped Contacts Listing…
2. Right-Click, and choose: Edit Contact
3. In the right column, Edit Grouping sub-tab, make changes to address and/or email type
4. Press button: Edit Contact
Delete Grouping
1) In the Grouped Contacts Listing…
2) Right-Click, and choose: Delete
3) Confirmation window appears
4) Press button: Yes, delete
End To End Encryption (E2EE)
In the left navigation bar, click the 12th icon to open the Encryption Keys Page.
Overview
End To End Encryption (E2EE) means that your message is encrypted on your device and is not decrypted until received on your contact’s device. Thus, the message is safe during the long journey thru the scary internet.
The encryption ‘Keys’ (Asymmetric) are created and managed by you, the user. Quantanon is different from all other E2EE systems in that regard. We do not believe that ‘Key Servers’, ‘Automatic Key Managers’, ‘Cloud Key Creation’, can be 100% safe. If some other entity created your keys, then that entity could have access to your keys. Even if this is untrue, better safe than sorry, right? The others use the cloud and servers in order to eliminate the so-called ‘hassle’ of Public Key exchange, a process we have made almost negligible (see below).
Quantanon is also on the leading edge of technology, as our encryption methods are the latest ‘Quantum’ resistant algorithms. As quantum computing is coming in the near future, the usual encryption methods will become ‘crackable’. Our methods are NIST recommended to be quantum resistant by using ‘lattice’ algorithms.
Definitions
Symmetric Encryption
Uses a password to encrypt and decrypt data. Can encrypt large amounts of data quickly. We use this to encrypt your email message and any non-image attachments. Quantanon generates a long, one-time use password for the symmetrical encryption process. Symmetrical encryption is quantum safe.
Asymmetric Encryption
Utilizes a Private/Public Key matched set. Encryption is slower and can only handle small amounts of data. We use this to encrypt your symmetrical encryption password, which is then sent along with your encrypted message. The symmetrical password is encrypted with the Public Key and is decrypted with the matched Private Key. After the symmetrical password is decrypted, it is then used to do the actual decryption of the original message and any non-image attachments.
How Quantanon E2EE Works
General scenario.
Each person, generates a Personal Key set consisting of Private and Public Keys. These keys are ‘matched’, in that when something is encrypted using a Public Key, then only the matching Private Key can decrypt. Public Keys can be distributed freely into the world, but the Private Keys are not sent out into the world freely. For 2 people to use E2EE, each person after generating a ‘Personal Key Set’, then exports the Public Keys to the other person. The sender encrypts the message symmetrically with a random generated password. Then the password is encrypted using the other person’s Public Key. Upon receipt of the encrypted message, the decryption of the encrypted symmetrical password is performed using the matched Private Key. The decrypted password is then used to decrypt the message and any non-image attachments.
Specific scenario.
Bob wishes to send Jane a Quantanon E2EE email message. He will need Jane’s Public Keys.
Key Management Steps:
1) Jane, in the Encryption Keys page, selects the tab: Key Sets – Personal Email Accounts
2) She selects her email account the clicks ‘Create Key Set’ (Keys are stored fully encrypted)
3) The Key Set listing shows: Account name, Private Keys(2), Public Keys(2), Digital Signatures for each key
4) She will not create these account keys again, even in another of her devices, just this one time
5) Jane now selects the tab: Public Keys – Export To Contacts
6) She selects contact Bob, selects her account Public Key set in the listing, then clicks ‘Export’
7) The Public Key set is sent via email attachment to Bob (attachment also encrypted)
8) She repeats the export process for any other contacts
9) Bob receives the email with attachment: PublicKeySetEnc.json
10) Bob clicks button ‘Import Key Set’ and he is good to go
Send Encrypted Message Steps:
1) Bob clicks the ‘New’ button for a new email, then the ‘Contacts’ button
2) Jane’s name shows, along with a small lock icon, meaning that her public keys are present and can send encrypted
3) Bob composes message and adds any non-image attachments
4) Bob checks box ‘Send Encrypted’ (next to the ‘Send Email’ button)
5) Bob clicks ‘Send Email’
6) Jane receives encrypted email which is automatically decrypted
7) Her lower message bar shows decryption status and if signature verification was successful
Encryption Keys Window
Tab: Key Set – Personal Email Accounts
As the name suggests, this is where you manage your keys. You need to create your Personal Key Set consisting of matching pairs of Private and Public keys. This is done only once per each of your email accounts – Even if you have more than one device. This way no matter which device you use, the same encryption/decryption with your contacts will work properly.
Section: Create Key Set For Your Account(s)
1) Select your desired account
2) Press ‘Create Key Set’
3) Key Set is created and shown in the right column listing (2 Private and 2 Public)
4) Each key has a ‘digital signature’. This value can be compared across any and all devices, both yours and contacts
5) Digital signatures must be the exact same value, else there might be a ‘man-in-the-middle’ compromise
6) You do NOT create a Personal Key Set again for this email account address, even on another device of yours
Note: When you create your Personal Key Set, the Public Keys will also show in the ‘Import From Contacts’ tab listing. This is done so you can send encrypted messages to yourself.
Section: Export Key Set to Yourself
This is used to send the full Key Set to another of YOUR devices only. This is because the same encryption keys must be used in order for the encryption/decryption to work with all of your contacts, from all of your devices.
1) Enter a 16+ character password and remember it (it is not saved anywhere)
2) Select desired account Key Set from listing
3) Press ‘Export’
4) The selected account will receive the email with encrypted attachment: PersonalKeySetEnc.json
5) On the other device, select the email
6) Enter the password, then press ‘Import Key Set’
7) All done
Section: Key Set Deletion
Key Set deletion should never be required. This option is included only for completeness sake. If an existing Key Set is deleted, then all your contacts will need to delete the Public Keys from you and all existing encrypted emails will become unreadable. You would need to create a new Personal Key Set and re-export like before. So be very sure you want to do this.
Section: Key Sets Listing: 4 Keys Per Account
Listing shows all your Personal Key Sets. Each set showing the 4 keys and their digital signatures.
Section: Important Read Me
Please read this section before doing anything in this tab.
Tab: Public Keys – Export To Contacts
After you have created your Personal Key Set, you need to export the Public Keys to each contact that you wish to encrypt emails with. Your contact will then use your Public Key Set to encrypt the message to you, where you will decrypt the message with your Private Key Set. Of course, your contact will need to export their Public Key Set to you, so you can send encrypted messages to them.
Section: Export Public Keys To A Contact
1) Select desired contact
2) Press ‘Export’
3) Exported details now show in the listing below
Section: Exported Public Keys Contact Listing
Shows exported Public Key Set details.
Section: Public Key Listing: 2 Keys Per Account
Shows your Public Key Sets. Click on desired set when exporting.
Section: Important Read Me
Please read this section before doing anything in this tab.
Tab: Public Keys – Import From Contacts
This tab shows the imported Public Key Sets from your contacts. These are the folks that you can send encrypted emails to, using their Public Keys to encrypt and they will use their Private Keys to decrypt. When you create your Personal Key Sets, the Public Key portion is also listed here, so you can send encrypted emails to yourself.
Section: Imported Public Key Listing
Shows your imported and person Public Key Sets. These are the contacts that you can send encrypted emails to. If you ‘Delete’ any of these, you would need to re-import in order to resume encryption. This action would only be necessary, if your contact changed their own Personal Key Set.
Section: Important Read Me
Please read this section before doing anything in this tab.
About Public Key Sharing
Much of the too-do of the other encryption using apps, is trying to eliminate the actual physical need to share the Public Keys. This requires the use of ‘Key Servers, Cloud Servers’ and the like. Do you really trust this? We believe that YOUR keys should only be created and managed by YOU.
The Quantanon process of Public Key exchange is very quick and easy. The exporter just selects a contact and Public Key set in the listing and clicks a button. Upon receipt of the email, the contact just clicks a ‘Import Key Set’ button and it is done. Maybe 30 seconds on each end, so no hassle at all.
Compose
To compose a new email, click on the + NEW button (upper-left)
The COMPOSE window opens
Row 1
Send Button
Click when ready to send email
Encrypt Checkbox
Check box for E2EE to valid recipients
If you have Public Keys imported from any of your contacts, they will show in the contact select list with a little ‘lock’ icon.
If any contacts are ‘non-encryptable’, you will first get an alert window, showing you these contacts. You then have to option to cancel the sending. If you don’t cancel, those contacts will receive the email non-encrypted.
Draft Button
Click to save unsent email to drafts folder
Cancel Button
Click to cancel current composed email
Reply Checkbox with Date
Check and select date to add to email, notifying recipient of a ‘Requested Reply by <date>’
Expiry Checkbox with Date
Check and select date for this email to expire for recipient
Recipient will be unable to forward, view header, save to HTML file
Message will have ‘Secured Message’ watermark
Message is encrypted, preventing reading in another email client or browser
Row 2
Email Send Type
Toggle thru choices of: To, Cc, Bcc
You can change this in your recipient list, by right-clicking the contact and making the change.
Contacts Button
Click to open list of contacts, select, then click button: Add Contact(s)
Group Contacts Button
Click to open list of pre-designed contact groups, select group to add all contacts
Groups are created in the Manage Contacts module, 6th icon in the left panel
Recipients Count
Just a notice of how many contacts are being sent to
+ New Button
Add in a new contact for this email and your contact list
This can later be edited in the Manage Contacts module
Row 3
Recipient listing
Right-click to edit send type
Left-click to remove a recipient
Row 4
Snippet and Placeholder Button, Subject line
Click, select desired subject item to add to subject line
View, create, edit subject snippets and placeholders in the Snippets – Placeholders module, 13th icon in left panel
Row 5 (double row)
2 rows of formatting buttons and options for your message
Row 6
Composition Tab, Ai Tab, Ai Help
Tab: Compose
Create and format your regular message here
Compose tab button: Add a signature, snippet or placeholder
Compose tab button: Add attachment (method 1 below)
Compose tab button: Add system file to send to another of your devices
Compose tab attachment size box: Keep your total size 25 mb or less
Tab: Ai
Use Ai tab button to select an Ai assistant to help compose your message. When done, click the ‘Copy’ button there and then paste into the main Compose tab. You can then continue to edit as usual.
Tab: Ai Help
Read the information in this tab for help
Add Attachments – 2 Methods
1. Click tab button: Browse and select attachments
2. Drag n drop attachments into the editor area
Send Clickable Link
We offer you 2 quick methods for doing this.
For example, you have a webpage open and want the send the site (URL address) as a link:
Method One
1. In Chrome, click the top-bar Copy Link button
2. Paste into message area (press CTR-V or right-click and select PASTE)
3. Click the SELECT ALL format button and the entire link is selected
(use SELECT ALL only if the link is the only item in message area, otherwise select it manually with the mouse)
5. Click button: Text to Link. The URL text is converted into a clickable link for your recipient
Method Two
1. In Chrome, click the top-bar Copy Link button
2. In the format bar, click button: Paste URL
3. The link is pasted as a clickable hyperlink
Link Cleaning
Link cleaning is enabled in Settings > Security Related Settings
If enabled, then the URL is cleaned of social media/analytics tracking garbage. You have done your part in stopping the tracking trail.
Here are a couple of examples:
Links not cleaned
https://www.greatfood.com/recipes/tropical-sweet-and-spicy-pork-tenderloin/?_cmp=quickdinners&_ebid=quickdinners392025&_mid=403337&ehid=ede84afc8826876fdef8a1624000c276276e4266&os_ehash=ede74afc8824876fdef9a1624000c276275e4266
https://www.skhotsauce.com/?fbclid=IwAR4KqWBFKNFHyp3Y5rc0Kusms5LXCdKjZd4Je8VbIMUuQ12TdbqowQct6NA
Links cleaned
https://www.greatfood.com/recipes/tropical-sweet-and-spicy-pork-tenderloin/
https://www.skhotsauce.com/ (note in this one, the ‘fb’ is how Facebook tracks clicked on advertisements) – NO WAY !!!
Snippets and Placeholders
To compose a new email, click on the + NEW button (upper-left)
The COMPOSE window opens
Add Contact(s)
Method 1
Click the button: Contacts, select from the list, click button: + Add Selection(s)
To delete an added contact, just click it twice in the list
Method 2
On the far right of the window, click button: +Add Contact
Enter contact info and check if is a Favorite
Click button: + Add Contact
The contact is added to the send list and your contact file
Method 3
Click the button: Grouped Contacts
If you have created any contact groups, the group name will show as a selection
Email Send Type
This is the To-Cc-Bcc copy send options.
You can select this in the toggle button, just left of the Contacts drop-down list
You can change this in your recipient list, by Right-clicking the contact and making the change.
Send Encrypted
If you have Public Keys imported from any of your contacts, they will show in the contact select list with a little ‘lock’ icon.
Checking the box: Send Encrypted will encrypt the message to the recipient(s)
If any contacts are ‘non-encryptable’, you will first get an alert window, showing you these contacts. You then have to option to cancel the sending. If you don’t cancel, those contacts will receive the email non-encrypted.
The Message
Type your subject and message into the appropriate boxes
You can click the ‘Quick Sub’ button and select a short subject topic
To format your message text, SELECT IT, then use any of the available format buttons in the row
Request Reply
At the top, is a check box: Request reply by: <select a date>
When checked, this request will appear in your sent message
It is up to the recipient if/when to reply
The Message with Ai
Tab: Compose
Create and format your regular message here
Tab: Ai Compose
Use selected Ai assistant to help compose your message. When done, click the ‘Copy’ button there and then paste into the main Compose tab. You can then continue to edit as usual.
Tab: Ai Help
Click button: Ai Service Select and choose desired Ai assistant
Read the information in this tab for help
Add Attachments – 2 Methods
1. Click button: Attachment Icon (bottom-left), and browse for attachments
2. Drag n drop attachments into the editor area
Send Clickable Link
We offer you 2 quick methods for doing this.
For example, you have a webpage open and want the send the site (URL address) as a link:
Method One
1. In Chrome, click the top-bar Copy Link button
2. Paste into message area (press CTR-V or right-click and select PASTE)
3. Click the SELECT ALL format button and the entire link is selected
(use SELECT ALL only if the link is the only item in message area, otherwise select it manually with the mouse)
5. Click button: Text to Link. The URL text is converted into a clickable link for your recipient
Method Two
1. In Chrome, click the top-bar Copy Link button
2. In the format bar, click button: Paste URL
3. The link is pasted as a clickable hyperlink
Link Cleaning
Link cleaning is enabled in Settings > Security Related Settings
If enabled, then the URL is cleaned of social media/analytics tracking garbage. You have done your part in stopping the tracking trail.
Here are a couple of examples:
Links not cleaned
https://www.greatfood.com/recipes/tropical-sweet-and-spicy-pork-tenderloin/?_cmp=quickdinners&_ebid=quickdinners392025&_mid=403337&ehid=ede84afc8826876fdef8a1624000c276276e4266&os_ehash=ede74afc8824876fdef9a1624000c276275e4266
https://www.skhotsauce.com/?fbclid=IwAR4KqWBFKNFHyp3Y5rc0Kusms5LXCdKjZd4Je8VbIMUuQ12TdbqowQct6NA
Links cleaned
https://www.greatfood.com/recipes/tropical-sweet-and-spicy-pork-tenderloin/
https://www.skhotsauce.com/ (note in this one, the ‘fb’ is how Facebook tracks clicked on advertisements) – NO WAY !!!
Read
Email Listing
Emails colored BLUE are new, unread, and turn to BLACK when read.
Mode: Read or Select
The app starts in READ mode, where you can:
1. LEFT CLICK on an email in the listing to read (showing in the right column).
2. RIGHT CLICK on an email to bring up a context menu with options:
Delete
Archive
Spam
Mark Unread
Flag
Unflag
Note: On all accounts, we have created a folder ‘Archive’ which is used for all archiving actions
To change to SELECT mode, where you can select multiple emails, click the ‘Check Mark’ mode button at the top of the email listing.
Then you can perform these actions on all selected emails (using buttons above the listing):
Delete
Move
Spam
Mark Read
Mark Unread
Controls Above Email Message
Delete
Delete current email from view and listing to Deleted/Trash folder
Move
Move to desired folder
Archive
Move email to the folder ‘Archive’
Reply
Click to reply to sender
Forward
Click to forward this email to recipients you choose
Reply All
Click to reply to all who received this same email
Mark as spam
Click to move to spam folder where servers are supposed to remember this action
Mark Unread
Change status of this email to ‘Unread’
Flag
Mark as important, flag will appear in listing
Unflag
Remove important flag
View Header
Click to view full header and IP origins, useful for forensic examinations
Save HTML File
Click to save current email contents (html content) to a HTML file (name of your choosing)
Then, you can dbl-click this saved file to open in your default browser.
In the browser, you can then select PRINT…
Tracking Pixel Found Status Bar
This notification bar is just above the email message content.
It displays the Tracking Pixel Found status and an ‘Unblock’ button.
If tracking pixels are found in a message, the notification will show:
“Tracking Pixels Found – Status: BLOCKED, with a button: Unblock”
If you find that something in the message does not work properly, such as a clickable link or image, you can then click the Unblock button, and re-select the email from the listing.
When you ‘Unblock’, the sender’s address is placed in a ‘Pixel Safe Sender’ file to avoid future pixel blocking.
To manage pixel blocking status, in the left navigation bar, click the 11th icon to open the Pixel Track page.
+ Add Sender to Contacts
Click this button to quickly add the message sender to your contact file.
View and edit contacts in the page Manage Contacts (left column, 6th icon)
+ Task
Click this button to quickly add a task while still in the message.
View and edit tasks in the page Tasks/Reply Requests (left column, 2nd icon)
+ Reply Reminder
Click this button to add a reminder to yourself, to reply to this email on/before a date of your choosing.
When the reminder is added, the email in the listing will have the subject colored RED with a reminder icon.
View and edit reminders in the page Tasks/Reply Requests (left column, 2nd icon)
Task and Reply Status Icons
Lower-Right of the main window shows status icons for Tasks and Replies.
Status icons: Future, Today, Past
Whenever there is a ‘Today’, the ‘Task – Reply Requests’ icon in the left column colors YELLOW.
Read Email Authentication
Every opened email is checked for modern message authentication. This is a check against spoofing, phishing, and impersonation. The results are shown in a line, just above the ‘+ Sender to Contacts’ button, as follows:
If ok: SPF/DKIM/DMARC/CompAuth – Authenication: PASSED (in green)
If not ok: SPF/DKIM/DMARC/CompAuth – Authenication: FAILED (in red), along with a detailed message alert.
What are they?
SPF – Sender Policy Framework
Verifies that the sending server is authorized to send on behalf of the domain, where the domain ownder has a list of allowed IP addresses. If the IP is not in the list, SPF: Fail
DKIM – Domain Keys Identified Mail
Ensures mail has not been tampered in transit and was sent by claimed domain. The sent email has been signed with a private key and the recipient domain’s public key is used to verify signature. If not verified, DKIM: Fail
DMARC – Domain Message Authentication, Reporting and Conformance
Instructions to the server if SPF or DKIM fails, based on the domain owner’s policy. Can be set to Fail.
CompAuth – Microsoft Service Authentication
Provides additional layer of trust based on the above 3 items and internal heuristics. Can fail and gives reason codes.
For full header info, click the ‘View Header’ button in the top row.
Folders
In the left navigation bar, click the 5th icon to open the Folders Page
Create New Folder
1. Select tab: Create Folder
2. Enter new folder name
3. Check ‘Create as subfolder under:’, if desired, and choose parent folder in list
4. Click button: + Create
Rename Folder
1. Select tab: Rename Folder
2. Select folder to rename from the list
3. Enter new folder name
4. Click button: Rename
Delete Folder
1. Select tab: Delete Folder
2. Select folder to delete from the list
3. Click button: Delete
Delete Warning: Any emails in delete folder will also be deleted
System Folders Enable
If you desire seldom used system folders, you can enable them here
Outlook
1. Scheduled
2. Notes
Gmail
1. All Mail
2. Important
3. Starred
4. Scheduled
Labels
Groups are unique to Quantanon and are a fun, easy way to sort by groups you set up in advance. The ‘Groups’ button is located just above the email list and the current group is shown just to the right of the button.
To select a group, click the button: Group, select your group name, then any email addresses set to that group will be filtered and shown in the list.
Manage groups in the Groups page, left navigation bar, click the 7th icon down.
Grouped Address Listing
This shows your grouped email addresses with the group name
To delete, select the address, then click button: Delete
Group Names Manager
To ADD a group name, enter the name in the text box, click button: Add
To DELETE a group name, select the name in the listing, then click button: Delete
Add Address to Group
In the right column, Group An Address:
1. Select email from drop-down list
2. Select group name from drop-down list
3. Click button: Add
Groups Automatically Added
If you have any addresses in the following categories, they will be shown in the Group Name listing in the main window:
Flagged
Reply Requests or Remindeers
Auto-Sort and Priority Inbox
You may wish to have certain emails automatically sorted to a folder, bypassing the INBOX.
This is a useful function in managing your emails and keeping your inbox cleaner.
Manage auto-sorting in the Auto-Sort page, 8th icon down in the left navigation bar.
Add Sort Action
Email Address
1. Select from choices: Email Address
2. Select an address from drop-down list, or type it in manually
3. Select sort folder from drop-down list
5. Click button: Add
Domain
1. Select from choices: Domain
2. Manually, type in domain in format: *@domainname.com
3. Be sure you start with: *@
5. Click button: Add
After clicking Add, the entry will show in the left column listing
Delete Sort Action
1. Select item in the left column listing
2. Click button: Delete
Calendar – Tasks
In the left navigation bar, click the 2nd icon to open the Tasks – Reply Requests Page.
Create Task
1. Select tab: Create – View – Select Tasks
2. Enter Task Title
3. Enter Task Details
4. Select Date and Time
5. Click button: +Add Task
6. Task will now show in Tasks: List View and date will be circled in the Tasks: Calendar View
A task can also be added in the Read email screen, by clicking button: + Task
List view color coding
Blue: Future events
Red: Today’s events
Black: Past events
Edit Task
1. Right click task in List View and select: Edit Task
2. The Edit Task tab opens, showing the task details
3. You can edit: Details, Date, Time
3. Make your changes, then click button: Edit Task
Delete Task
1. Right click event in List View and select: Delete
Main Email Window Notifications
Task Today
1. Left navigation bar Task – Reply Requests icon turns YELLOW
2. Lower-right icon: Task Today shows a RED check mark
Task Future
1. Lower-right icon: Task Future shows a BLUE check mark
Task Past
1. Lower-right icon: Task Past shows a DARK GRAY check mark
Reply Requests / Reminders
There are 2 types of replies:
Reply Requests
These are generated in the NEW email compose screen.
At the top is a check box: Request reply by <select date>
The recipient’s email will have this notification and the subject line will be colored RED with a notify icon.
Reply Reminders
These are generated in the READ email screen.
Above the message, is a button: + Reply Reminder
Just select desired date.
The email in the listing will now be colored RED with a notify icon.
Manage Replies
In the left navigation bar, click the 2nd icon to open the Tasks – Reply Requests Page.
When there, select the tab: Replies Needed
List view color coding
Blue: Future replies
Red: Today’s replies
Black: Past replies
Edit Reply
You can only edit the date of the reply type: Reminder
1. Right click reply in List View and select: Edit Reply
2. The Edit Reply tab opens, showing the associated email and the current date
3. You can edit: Date
3. Make your change, then click button: Edit Due Date
Delete Reply
1. Right-click reply in List View and select: Delete
Main Email Window Notifications
Reply Today
1. Left navigation bar Task – Reply Requests icon turns YELLOW
2. Lower-right icon: Reply Today shows a RED check mark
Reply Future
1. Lower-right icon: Reply Future shows a BLUE check mark
Reply Past
1. Lower-right icon: Reply Past shows a DARK GRAY check mark
Adserver Tracking and Host File
All clicked links in received emails are scanned for known adserver trackers. These nasty items are hidden in the link code and you never see them when the new website is opened. These guys allow companies to track your online habits and commercial interests to try and force ads on you… constantly.
Here is an example of what is going on.
Clicked link in email:
https://1rvs.r.us-east-1.awstrack.me/L0/https:www.techknow.com%2F%2F10-marketplace-scams-to-watch-out-for
Clicked link opened in website that you see:
https://www.techknow.com/marketplace-scams-to-watch-out-for
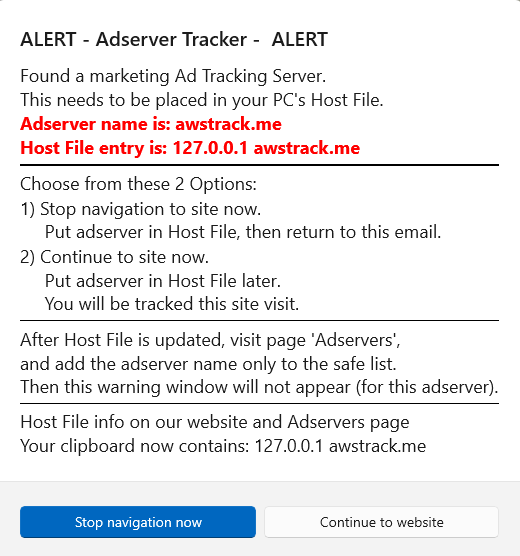
The adserver tracker here is awstrack.me that you never knew was there. Whenever one is found in a clicked link, a dialog window will show, alerting you of the problem, giving you 2 options:
1. Stop navigation to site, allowing you to put the adserver in your host file before returning to the email
2. Continue to site now, site will then track you. Put adserver in host file later
If you need to get to the site immediately or don’t care about tracking, use option 2.
Shown below is the alert dialog window.
Host File Info
The host file on you PC allows redirection of domains. You want to ‘redirect’ the clicked link from going to the adserver domain, and instead, direct back to your own machine, i.e., going nowhere! You add the redirect IP of 127.0.0.1 (your machine) to the adserver URL and put this line in your host file. This permanently stops the ad server from getting your personal info, but the link will still open to the desired website. You can add thousands of redirects to your host file.
Here are the steps:
1. Click Start button and locate Notepad in the apps listing
2. Rt-Click on Notepad > More > Run as administrator
3. In Notepad, File > Open, then navigate to: C:\Windows\System32\drivers\ect
4. If you don’t see the file Hosts, then in the lower-right dropdown, change Text documents (*.txt) to All files (*.*)
5. Select hosts, then Open
6. Type in the adserver redirect below the commented out lines (# ::1 localhost)
7. The host file redirect entry format is as this example:
The found adserver URL is: ad-space.net
The host file entry needed is: 127.0.0.1 ad-space.net
8. Save the file. File > Save
9. Just put more of these entries in as they occur, each on a separate line
Possible Host File Issues
If, when you try to save the host file and you get a ‘You don’t have permissions to save…’, it is probably because you did not open Notepad in Run as administrator mode.
You can also navigate directly to the host file using File Explorer (C:\Windows\System32\drivers\ect), then:
1. Rt-Click on hosts > Properties > Security tab
2. Click on each Group or user name, then click Edit to change permissions, checking all the ‘Allow’ boxes, and OK
3. If the host file did not show up in the File Explorer, then in the options bar, click View > Show > Hidden items
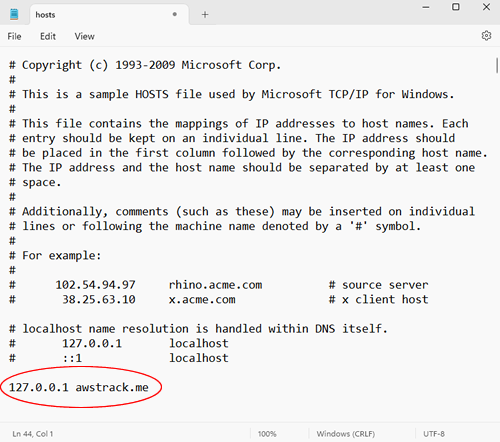
Here is what the host file should look like with the entry: 127.0.0.1 awstrack.me
Adserver Page
In the left navigation bar, click the 9th icon to open page: Adservers
On this page, you manage your adserver list.
When you have been alerted to an adserver and you have placed it in your Host File as outlined above, then you will want to add this adserver name to the list.
Once in the list, the alert dialog (for this adserver) will not appear again, as you are now safe.
Steps
1. In the ‘Add an Adserver’ box, type in the name WITHOUT the 127.0.0.1 prefix
2. Click button: + Add
Spy Pixel Tracking
All emails opened for reading are scanned for hidden tracking pixels. Recall, that these little gems send info about you back to the sender, supposedly in the name of advertising. If found, a pop-up alert will appear:
Options in the alert are (with option to remember choice for future emails from this sender):
Block Pixels
Normal Open (no block)
What we do – We always select Block Pixels and see if the resulting email is still ok, meaning that the content that we need to access is still good. Sometimes you may need a link that is blocked (not too common). So, if your email is good after choosing Block Pixels, go back and reopen the email, and this time check the option ‘Remember choice for this sender’, then click ‘Block Pixels’.
You can always see the pixel tracking status of your opened email by checkout the pixel status text box below the email message in the main read screen
Editing Pixel Action
You can edit an action that you have previously set for a particular email address in 2 ways:
1. Right-click on the email in the listing, and change the action
2. Open the PIXEL TRACK window, 3 dots (lower-left), and do the same
Oh, and here is an interesting article on this topic.
Phish Scanner
Complok automatically scans the text content of all messages for suspicious wordings that are commonly associated with phishing scams. If any are found, a popup will show and alert you.
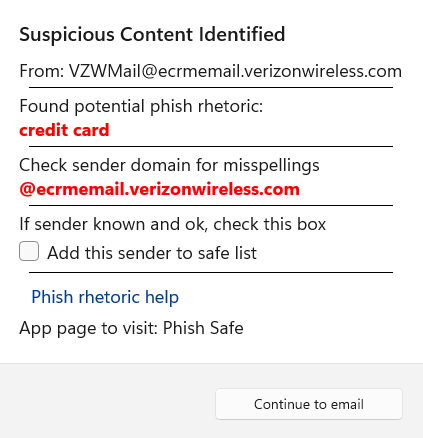
If the email is from a known, safe sender, click the button ‘Add sender to safe list’.
After that, you will not be notified again on any further emails from this sender.
Many phishing scams use an email address that is very close to the real company, so pay attention to that also. Look for slight misspellings and/or odd extra words in the string. Example:
Good one: accounts@bankofamerica.com
Bad one: accounts@banksofamerica.com, accounts@bankofamerika.com
Phish Reporting
Here are a few resources to report phish scams:
Anti-Phishing Working Group
Email: reportphishing@apwg.org
Social Security Scams to Office of the Inspector General
https://oig.ssa.gov/report/oig.ssa.gov/report
Federal Trade Commission
https://reportfraud.ftc.gov/reportfraud.ftc.gov
Suspicious Attachments
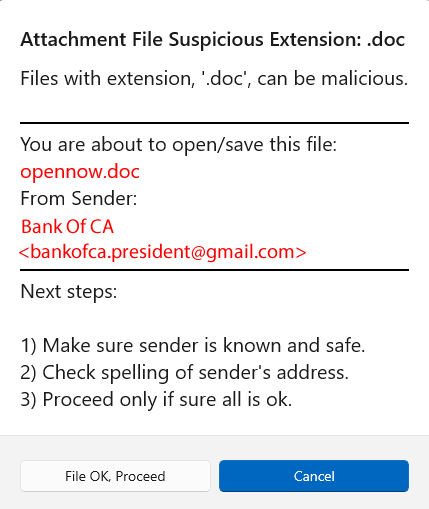
Thankfully, many providers also scan for these and block the email.
Please examine the screen below and see what will appear if suspicious attachments are found:
1. They will be listed in RED
2. A popup will appear to give you warning
Private Browser
The Quantanon Private Browser is, again, unique. It is completely isolated from Chrome, Edge or any other browser, and therefore, no history is saved or shown.
In the left navigation bar, click the 3rd icon down to open the Private Browser.
Printing
With the email you want to print showing:
1. Click button: Save HTML File (far upper-right, behind the 3 dots)
2. Choose file save location in the dialog that shows
3. File will be saved with extension: .html
4. Dbl click on saved file to open in browser
5. In browser, select ‘Print…’
6. Printer dialog opens with options and button: Print
Attributes
Thank you to FlatIcon.com for some of our nice icons.
FlatIcon
